dirtyZero IPA: Tweak iOS 18 - 18.3.2 without a Jailbreak with CVE-2025-24203
A new proof-of-concept app named dirtyZero is leveraging a recently discovered vulnerability, tracked as CVE-2025-24203, to modify protected areas of macOS and iOS systems. The exploit, uncovered by Ian Beer of Google’s Project Zero, enables limited write access to read-only memory pages—though with a critical caveat: it can only zero out data on these pages, unlike the more versatile MacDirtyCow exploit that allowed arbitrary writes.
Disclosed through Google Project Zero’s issue tracker, the vulnerability exploits a memory management flaw in Apple’s operating systems. Dubbed BEHAVIOR_ZERO_WIRED_PAGES, the exploit grants apps the ability to overwrite read-only kernel memory pages by resetting their contents to zero. While this restricts attackers from writing custom data, it still poses significant risks, as zeroing out critical system data could destabilize devices or disable security mechanisms.
Notably, the bug affects iOS versions prior to 18.4, though Apple’s iOS 18.4 release notes do not explicitly acknowledge a fix. This omission raises concerns that the patch may have been silently deployed, leaving users unaware of their device’s vulnerability status. Alternatively try mdc0 by misakaX developer.
dirtyZero IPA Download: Get the Newest Release
dirtyZero was released as an IPA package that can be installed using your favorite IPA Installer App. IPA is dedicated to standard sideloading apps on Apple devices. Download the latest version of dirtyZero IPA from the links available below. Once installed, you'll be able to customize your ≤ iOS 18.3.2 system.
dirtyZero: Tweak iOS 18 without a Jailbreak
The dirtyZero app demonstrates the exploit’s potential by targeting user interface elements on iOS. On devices running iOS 18.3.2 and earlier, it allows users to hide the Dock and Home Bar—features typically restricted by Apple’s system protections. Developers hint that future updates could introduce more tweaks, depending on the exploit’s versatility.
However, dirtyZero’s current capabilities highlight a broader issue: even limited write access to protected memory could enable malicious actors to manipulate system behavior or bypass security checks. While the app is labeled a proof-of-concept, its existence underscores the urgency of patching affected devices.
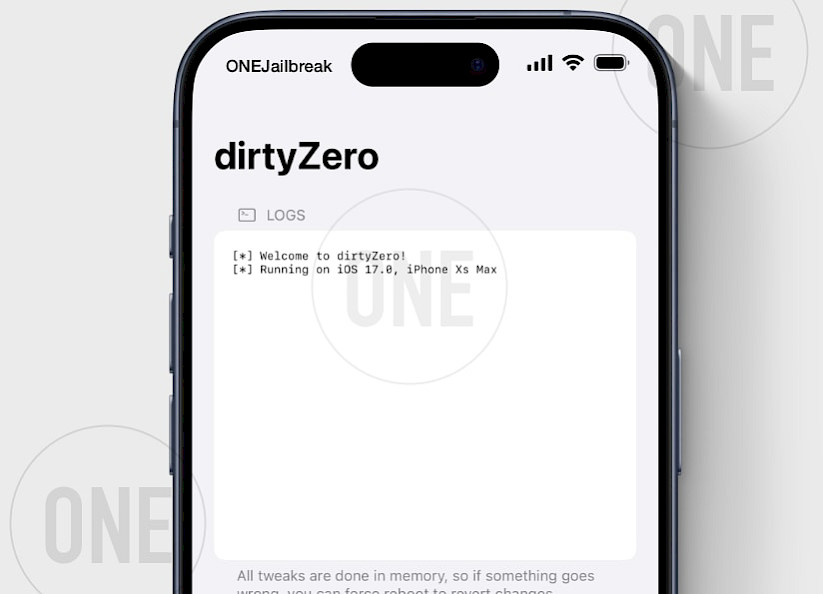
New tweaks with dirtyZero 1.0 Release
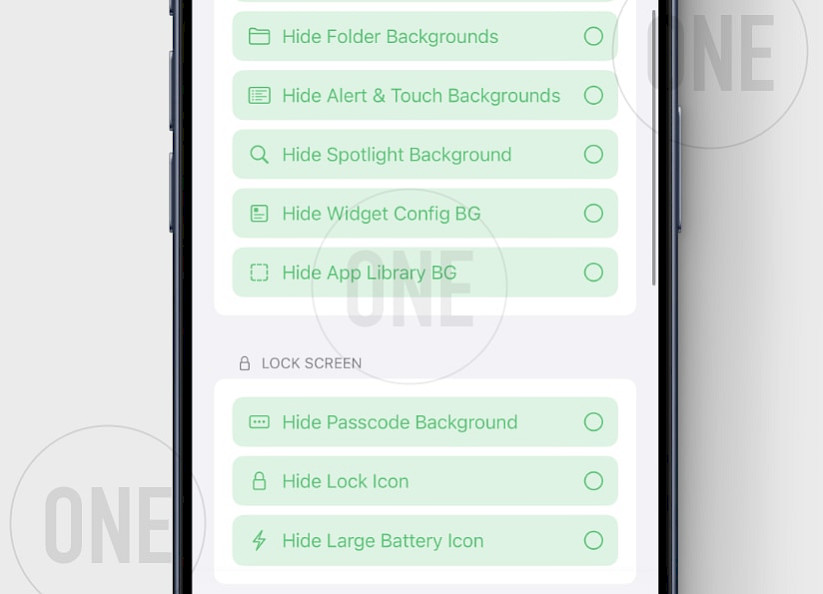
The dirtyZero app offers a range of customization options for tweaking iOS, focusing on enhancing user interface aesthetics and functionality. Under the "Springboard" section, users can hide elements like the dock, folder backgrounds, alert and touch backgrounds, Spotlight background, widget configuration background, and app library background, creating a cleaner and more minimalistic home screen.
Options to hide the passcode background, lock icon, and large battery icon further declutter the interface. The "Systemwide Customization" section includes toggles to hide notification and widget backgrounds, apply the Helvetica font systemwide, and remove emojis for a more uniform look. Users can also disable various sound effects, such as AirDrop ping, charge sound, low battery sound, and payment sounds, for a quieter experience.
Additionally, the "Control Center" settings allow users to disable the control center background, module background, brightness icon, and Do Not Disturb (DND) icon, providing a streamlined control center appearance. Each section includes "Apply," "Revert," and "Respring" buttons to save, undo, or refresh changes, giving users full control over their iOS customization.
Security Implications and Device Compatibility
The vulnerability affects both macOS and iOS, but the dirtyZero exploit currently targets iOS devices. Users running iOS 18.4 or later are likely protected, while those on older versions remain vulnerable. Apple’s vague release notes make it hard for users to confirm whether their devices are fully patched.
Although Apple seems to have addressed the issue in iOS 18.4, its lack of clarity leaves some uncertainty. Tools like dirtyZero highlight the fine line between customizing your device and keeping it secure.
For users, the best step is simple: update to iOS 18.4 or later and steer clear of unofficial tweaks that exploit vulnerabilities. For developers, dirtyZero shows that even “minor” exploits can cause real problems—and zero-day hunters are always on the lookout.
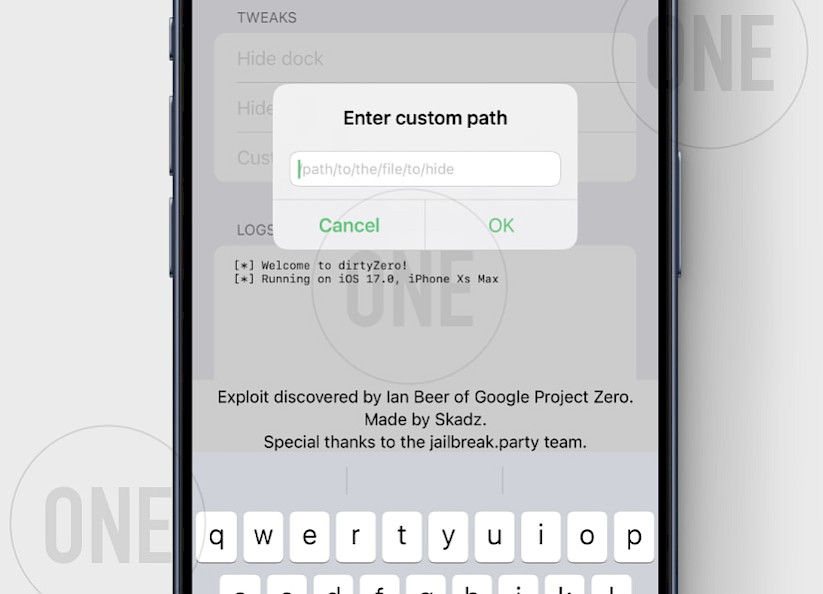
How to install dirtyZero IPA on iOS 18.3.2 and below
dirtyZero can be sideloaded on your iPhone or iPad using your favorite IPA installer. Download the most recent version of dirtyZero IPA and start tweaking your iPhone without the need to use a jailbreak. Please note that this is only a Proof-of-Concept tool.
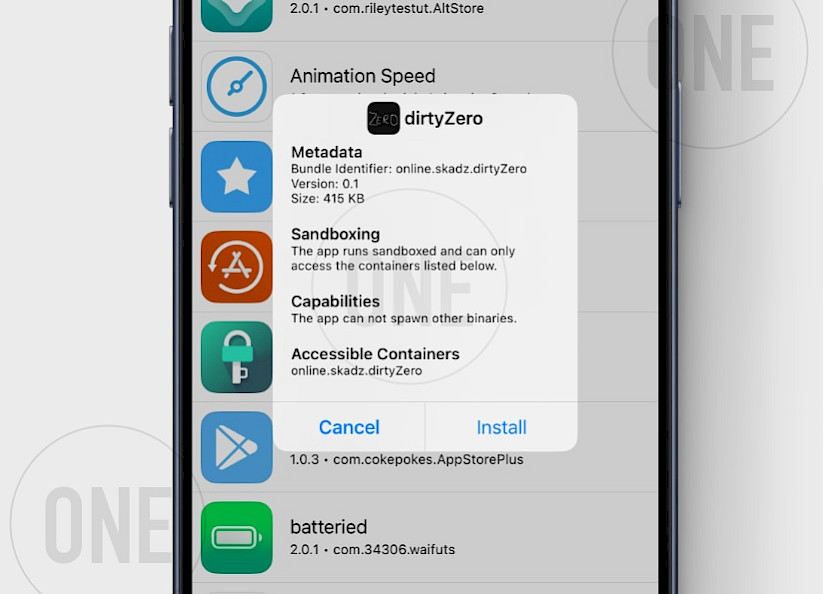
Here's how to install dirtyZero IPA on iPhone:
- Download the latest dirtyZero IPA for iOS 18.
- Install Sideloadly for Windows or macOS.
- Sideload dirtyZero.IPA by following the guide Installing IPA on iPhone.
- Open the dirtyZero App from your Home Screen.
- Repsting your device from dirtyZero 1.0.
Important: You must respring your iOS device to apply changes. To restore the original system settings, simply restart your device. (A respring refreshes the UI without a full reboot, while a restart clears all temporary modifications.)
How to Respring Your iOS 18 Device
Since the release of dirtyZero 1.0, the app has provided a streamlined solution for respringing your iOS device, eliminating the need for manual intervention.
Here's how you can respring your device manually on iOS.
Step 1. Open the Settings app from your Home Screen.
Step 2. Tap Display & Brightness, then select Display Zoom.
Step 3. Switch to the opposite option of your current setting:
- If set to Bigger Text, choose Standard.
- If set to Standard, choose Bigger Text.
Step 4. Tap Apply, then confirm by tapping the pop-up button.