MobSF Mobile Security Framework
Several tools are available for analyzing iOS apps and IPA files, catering to various needs such as pen-testing, malware analysis, and security assessments. Among these tools, the Mobile Security Framework stands out as a comprehensive solution, offering detailed insights into IPA files. With MobSF, users can generate comprehensive reports that provide insights into various aspects of the IPA file, including function calls, vulnerabilities, and potential risks that could compromise the security of the device. These reports are presented in an easy-to-understand format.
What is MobSF Mobile Security Framework?
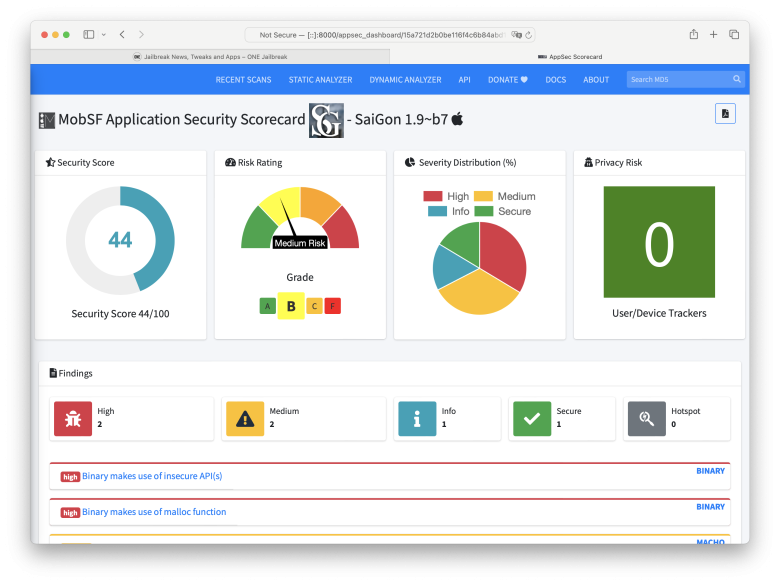
Mobile Security Framework (MobSF) stands as an advanced, comprehensive solution for mobile application security, encompassing automated iOS pen-testing, malware analysis, and security assessment capabilities. With MobSF, users gain access to a robust suite of tools designed to facilitate static and dynamic analysis, catering to a wide array of security needs.
MobSF serves as a versatile tool, ideal for diverse applications such as mobile application security assessments, penetration testing, malware analysis, and privacy evaluations. Its Static Analyzer supports popular mobile app binaries like IPA, alongside source code analysis, enabling thorough examination of application vulnerabilities and weaknesses.
In tandem, the Dynamic Analyzer extends support to iOS apps, providing a dynamic testing environment for interactive instrumented testing, runtime data analysis, and network traffic monitoring. This comprehensive approach ensures a thorough evaluation of an application's security posture across different stages of development and deployment.
One of MobSF's notable strengths lies in its seamless integration capabilities with DevSecOps or CI/CD pipelines. Through REST APIs and CLI tools, MobSF effortlessly integrates into existing workflows, empowering teams to incorporate robust security assessments into their development processes with minimal friction. This integration enhances security practices by enabling automated security checks and ensuring continuous monitoring throughout the software development lifecycle.
The latest version of the Mobile Security Framework (MobSF) introduces a plethora of enhancements across various fronts. Notable updates include the incorporation of an iOS Dynamic Analyzer featuring Corellium support, a revamped Dynamic Analysis setup catering to both Android and iOS platforms, and the unveiling of exposed iOS Dynamic Analysis REST APIs.
Additionally, an array of new Frida Scripts has been added to augment the functionality of the Android and iOS Dynamic Analyzers, alongside significant improvements in Frida support, spanning Injected Frida Code View, Injection, Spawn, Attach, and Session.
Among other improvements, the update enhances Android API Analysis rules, introduces Apksigner.jar fallback for signature parsing, streamlines MobSF scan REST API, and adds support for analyzing iOS Frameworks. UI enhancements are also prominent, with changes aimed at improving real estate utilization in both the AppSec dashboard and Static Analysis interface.
Moreover, this version boasts Corellium Reverse SSH connection compatibility, bolstered ARC and Stack Canary Checks in Mach-O Parsing, and Frida RPC Hooks support. Further refinements encompass Runtime Executable Tampering Detection, extensive documentation for the iOS Dynamic Analysis REST API, and enhanced capabilities for exporting Global Datatables in various formats such as PDF, CSV, and XLS.
Furthermore, the update introduces support for analyzing independent library files from APKs/IPAs, refactors library analysis relative path helpers, and reinstates RELRO checks for Android while incorporating Dart binary checks to mitigate Flutter false positives.
It also enhances stripped debug symbol checks for ELF and MachO using native OS tools and merges iOS Framework and Dylib Analysis. Notably, there are substantial performance improvements in Static Analysis report generation, particularly for APKs/IPAs with large datasets.
MobSF Beyta includes various bug fixes, such as addressing issues related to parsing DSA Public Key parameters for fingerprint calculation, and rectifying arbitrary file write vulnerabilities on Windows with apktool. Overall, this version signifies a significant leap forward in MobSF's capabilities, encompassing a wide spectrum of enhancements aimed at fortifying mobile application security.
How to install MobSF on macOS
To utilize the MobSF Mobile Security Framework on your Desktop, it's essential to have Python and pip installed. It's worth noting that MobSF dependencies specifically require Python version 3.10 to 3.1. To streamline the setup process, a dedicated setup script is available, enabling you to verify compatibility and install all necessary components seamlessly.
Info: For Windows users, a dedicated setup.bat file has been provided, simplifying the installation procedure further. By running this script, users can ensure that MobSF is properly configured and ready for use on their systems.
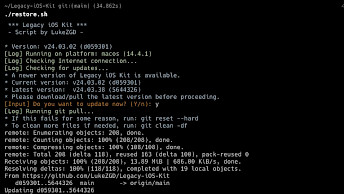
Step 1. Open the terminal app, clone the repository to local storage, and navigate into it.
git clone https://github.com/MobSF/Mobile-Security-Framework-MobSF && cd Mobile-Security-Framework-MobSF
Step 2. Add permission to run for run.sh and setup.sh files.
chmod +x ./run.sh && chmod +x ./setup.sh
Step 3. Execute the setup.sh script to install missing components.
./setup.sh
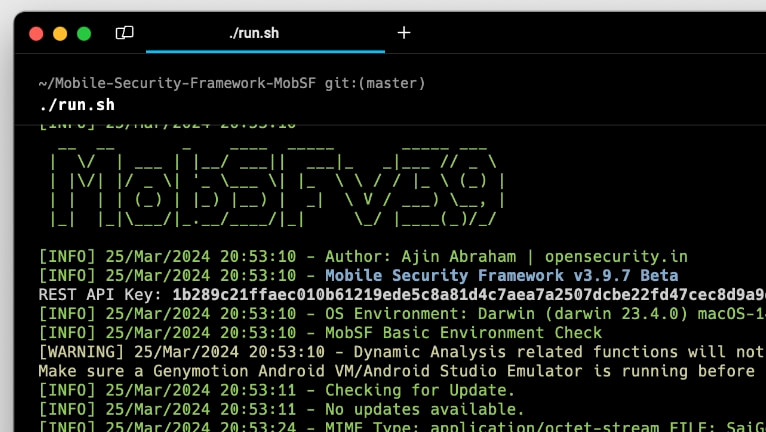
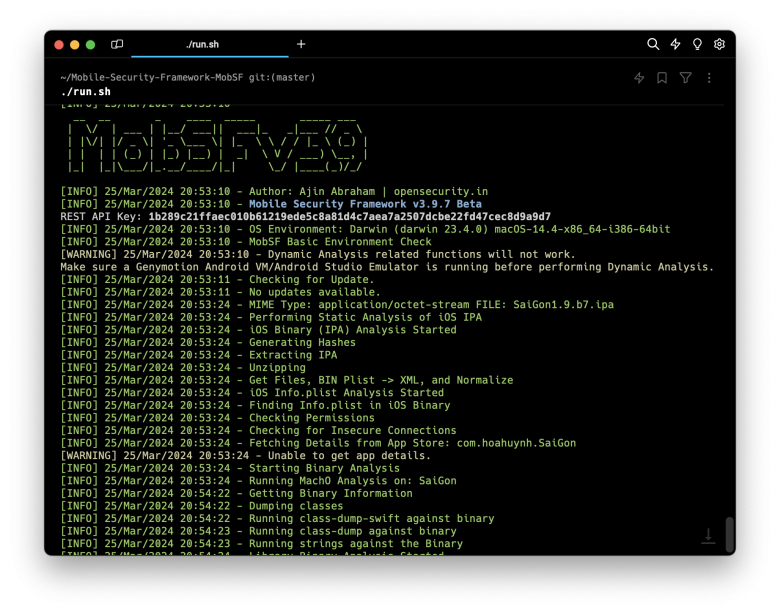
Step 4. Execute the run.sh script to run the MobSF application.
./run.sh
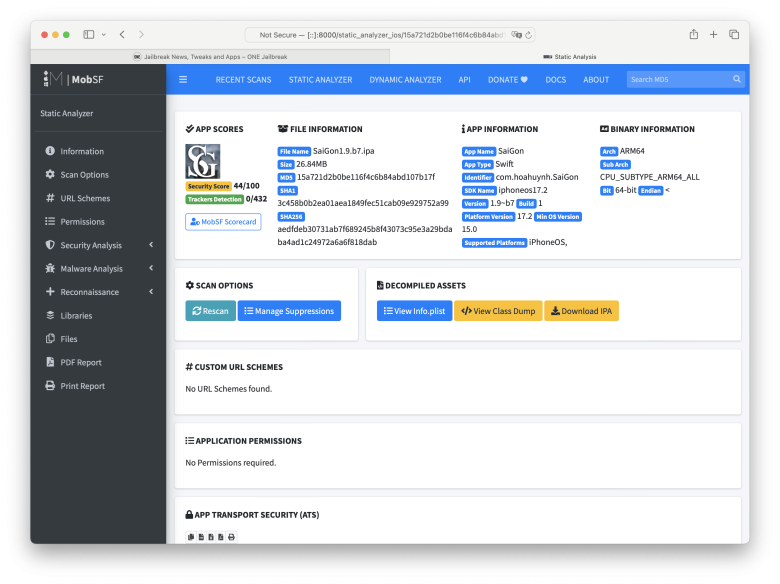
Step 5. Open the URL in your browser to view the MobSF Dashboard.
http://[::]:8000