mitmproxy reverse engineer toolbox for apps API on iOS
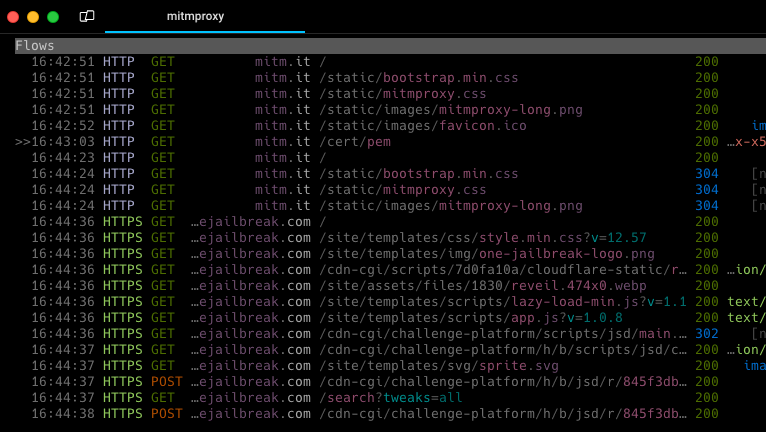
mitmproxy, developed by the Mitmproxy Project, is a powerful and interactive intercepting proxy that supports SSL/TLS and provides a console interface for handling HTTP/1, HTTP/2, and WebSocket traffic. This tool is particularly useful for capturing and analyzing all data exchanged between your iOS device and external servers, making it an invaluable resource for reverse engineering private APIs within applications.
Highlights:
- mitmproxy not only supports HTTP, HTTP/2, HTTP/3, but also other web protocols such as WebSocket, DNS, Generic TCP/TLS Proxy, and Generic UDP/DTLS Proxy.
- Python API allows you to write addons and scripts with API that offers full control over mitmproxy and makes it possible to implement your own commands.
- One of the main purposes of mitmproxy is the possibility to reverse engineer iOS app's private API with encryption by Man In the Middle (MITM) attack.
- mitmproxy is a command line tool, accompanied by mitmweb, which provides an intuitive web interface akin to Chrome's DevTools to monitor network traffic.
Download
mitmproxy can be installed on all popular desktop platforms including Windows, Linux, and macOS. For the first two, you can use a dedicated installer. mitmproxy for macOS is recommended to be installed through The Missing Package Manager for macOS – brew.
Overview
Mitmproxy serves as a comprehensive toolbox for reverse engineering the APIs of applications operating on iOS devices. It comprises three key modules: mitmproxy, mitmdump, and mitmweb. The mitmdump module functions as the command-line counterpart to mitmproxy, likened to tcpdump for HTTP. Meanwhile, mitmweb provides a user-friendly web-based interface for seamless interaction with mitmproxy's capabilities.
One of the principal benefits of mitmproxy is its capability to generate a root SSL certificate that can be installed on your iPhone device. This unique feature empowers you to decrypt HTTPS communications, enabling a comprehensive analysis of all app connections to servers.
This transparency is particularly advantageous for reverse engineering private APIs, as it facilitates a deep understanding of the underlying communication protocols. Additionally, mitmproxy can be utilized to uncover the specific private data being transmitted by the app to external servers, such as GPS location, device type, iOS version, and more.
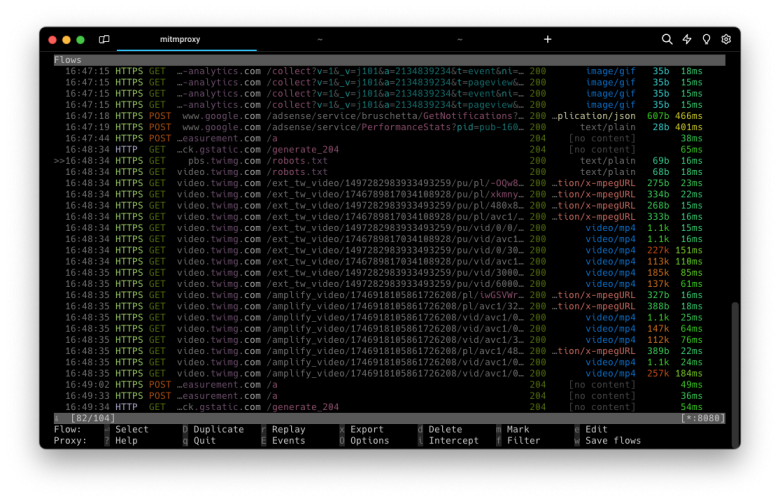
Indeed, another noteworthy capability of mitmproxy is its ability to intercept and modify requests before they are sent or received by the server. This functionality is especially valuable in the context of security penetration testing, as it allows users to inject custom code into the requests. This dynamic modification of requests provides a practical means to assess the system's resilience to various security vulnerabilities and helps identify potential weaknesses that may be exploited. mitmproxy's flexibility in altering requests enhances its utility as a powerful tool in the arsenal of security professionals and researchers.
Mitmproxy played a crucial role as one of the primary tools employed by Kaspersky Security Researchers during Operation Triangulation. Its capabilities were instrumental in decrypting HTTPS traffic, enabling the researchers to track and analyze the self-installing Messages malware on iOS devices that was designed to take over the iDevice without a trace.
Info: mitmproxy supports Windows, macOS, Linux, iOS, and Android devices.
Moreover, mitmproxy facilitates real-time monitoring and modification of requests, empowering dynamic adjustments on the fly during the interception process. It's worth noting, however, that the installation of a root SSL certificate does not grant the capability to intercept HTTPS traffic from Apple services, including iMessage. This limitation arises due to iOS implementing SSL pinning for enhanced security measures.
What's new:
- Add support for editing non text files in a hex editor.
- Add server_connect_error hook that is triggered when connection establishment fails.
- Add section in mitmweb for rendering, adding and removing a comment.
- Fix multipart form content view being unusable.
- Documentation Improvements on CA Certificate Generation.
- Make it possible to read flows from stdin with mitmweb.
- Update aioquic dependency to >= 1.0.0, < 2.0.0.
- Fix a bug where async client_connected handlers would crash mitmproxy.
- Add button to close flow details panel.
- Ignore SIGPIPE signals when there is lots of traffic. Socket errors are handled directly and do not require extra signals that generate noise.
- Add primitive websocket interception and modification.
- Add support for exporting websocket messages when using
Mitmproxy offers the capability to intercept both HTTP and HTTPS requests and responses, allowing dynamic modifications in real time. Users can save entire HTTP conversations for subsequent replay and in-depth analysis. The tool also supports the replay of the client side of an HTTP conversation and can reproduce HTTP responses from a previously recorded server. Additionally, mitmproxy features a reverse proxy mode for forwarding traffic to a server.
On macOS and Linux, it provides a transparent proxy mode. For scripted alterations to HTTP traffic, mitmproxy supports Python, enabling users to make customized changes. Furthermore, SSL/TLS certificates for interception are generated on the fly, enhancing the tool's flexibility and adaptability to various security scenarios. Source code can be found on GitHub Repository.
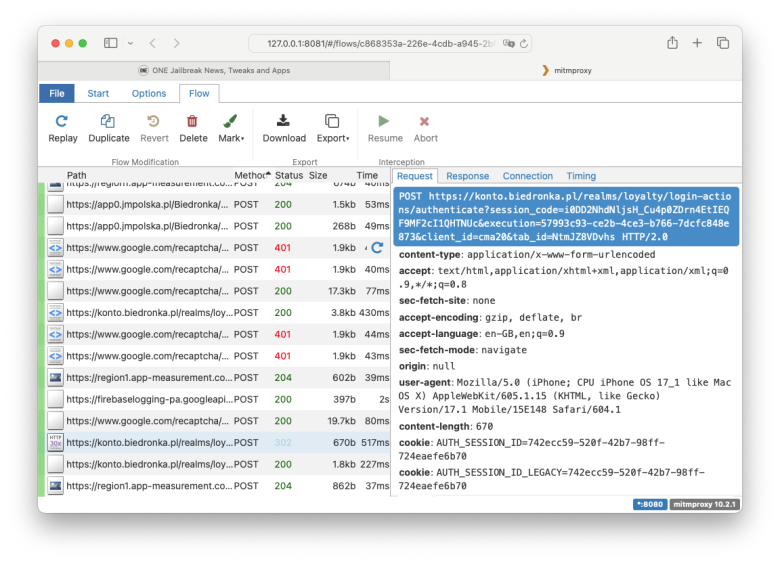
Mitmweb serves as mitmproxy's web-based UI, providing an interactive platform for the examination and modification of HTTP traffic. Distinguishing itself from mitmdump, mitmweb retains all flows in memory, making it well-suited for the capture and manipulation of samples.
Mitmdump serves as the command-line counterpart to mitmproxy, offering tcpdump-like functionality. This tool enables you to observe, record, and programmatically modify HTTP traffic. For comprehensive documentation, refer to the output provided by the --help flag.
How to install mitmproxy on macOS
The preferred method for installing mitmproxy on macOS is through Homebrew. Alternatively, standalone binaries of mitmproxy for macOS can be downloaded from the official mitmproxy.org webiste. Please note that for Apple Silicon, Rosetta is required.
/bin/bash -c "$(curl -fsSL https://raw.githubusercontent.com/Homebrew/install/HEAD/install.sh)"
brew install mitmproxy