Frida: Reverse engineering toolkit for iOS applications
Developed by Ole André V. Ravnås, Frida stands out as one of the premier tools for debugging, reverse-engineering, and hacking into iOS apps. Its robust API empowers developers to craft their automated scripts, enabling a range of tasks, including decrypting apps from iOS devices. The most recent release of Frida comes with a lot of improvements and bug fixes. It also offers a brand new ApiResolver for Swift.
What is Frida?
Frida is a toolkit for security researchers allowing them to reverse engineer applications running on iOS, tvOS, and watchOS. Use it to inject your own scripts into black box processes. Hook any function, spy on crypto APIs, block jailbreak detection functions, activate premium features or trace private applications. Frida can find files, classes, and functions inside any application.
It is advisable to integrate the toolkit into an iOS app to facilitate real-time debugging and code modification. The optimal method for leveraging Frida on iOS involves utilizing a jailbroken device and directly installing all required packages on your iPhone. However, it's worth noting that it is also feasible to run Frida without a jailbroken device or the need for patching the app.
Frida can be likened to the Greasemonkey Firefox add-on but tailored for native applications. This toolkit empowers you to not only alter the appearance of applications but also inject your custom code to modify their behavior. Additionally, Frida provides its own API, enabling the development of tweaks that automate the application modification process. For instance, you can manually decrypt iOS apps or streamline the process using a decryption script.
It can be used to as a Wireshark on steroids with support for sniffing encrypted protocols. Frida could even manipulate function calls to fake network conditions that would otherwise require you to set up a test lab. This is a powerful dynamic instrumentation toolkit for iOS.
Frida's core is crafted in C and injects QuickJS into the target processes, enabling your JavaScript code to execute with unrestricted access to memory. It can hook functions and even invoke native functions within the process. The communication between your application and the JavaScript running in the target process is facilitated through a bi-directional channel.
Utilizing Python and JavaScript provides a conducive environment for swift development, backed by a secure API. Frida aids in quickly identifying errors in JavaScript, presenting exceptions instead of causing crashes. If Python isn't your preferred language, worry not. Frida supports direct usage from C, and built upon this C core, there are multiple language bindings available, including Node.js, Python, Swift, .NET, Qml, Go, among others.
Frida for iOS is a powerful toolkit that can be used to penetrate iOS apps including Local Data Storage, Jailbreak Detection, Excessive Permissions, Runtime Manipulation, Anti Anti Hooking/Debugging, Binary Protection, Touch/Face ID Bypass, Phishing, Side Channel Data Leakage, IPC Issues, Broken Cryptography, Webview Issues, Network Layer Security, Application Patching, Sensitive Information in Memory. DVIA v2 allows you to test your skills.
With just a few lines of C, you can execute JS within a runtime that grants complete access to Gum's APIs. This empowers you to hook functions, enumerate loaded libraries along with their imported and exported functions, read and write memory, and scan memory for patterns. The Flex toolkit operates under three distinct models: Injected, Embedded, and Preloaded.
What's new
- Updated Frida to the latest version.
- Improve stability on multiple fronts.
- Improve symbolicator cache invalidator logic.
- Handle signed pointers.
- Overall improvements and bug fixes.
Frida's Gadget serves as a shared library designed for loading into programs requiring instrumentation when the Injected mode is impractical. Implementation can be achieved through various methods, such as modifying the source code of the program, patching it or one of its libraries (e.g., using tools like insert_dylib), or leveraging dynamic linker features like LD_PRELOAD or DYLD_INSERT_LIBRARIES.
A standout feature within the Frida toolkit is its potent code-tracing engine – Stalker. This engine enables the tracking of threads, capturing not only every function but also every block and even every executed instruction. Stalker currently supports the AArch64 architecture commonly found on mobile phones and tablets running iOS.
Alternatively, consider employing FLEX, an in-app debugging and exploration tool designed for iOS. Several jailbreak tweaks serve as FLEX wrappers, enabling you to debug iOS, hook into systems, and craft your custom modifications and tweaks without relying on an API. Notably, FLEXList and FLEXall stand out as among the best options available for this purpose.
RootHide Bootstrap will additionally incorporate support for Frida, facilitating the debugging of all enabled apps. This tool allows users to apply tweaks to almost all apps without the need for a jailbreak. Springboard tweaks are not currently supported.
Installing Frida on Desktop
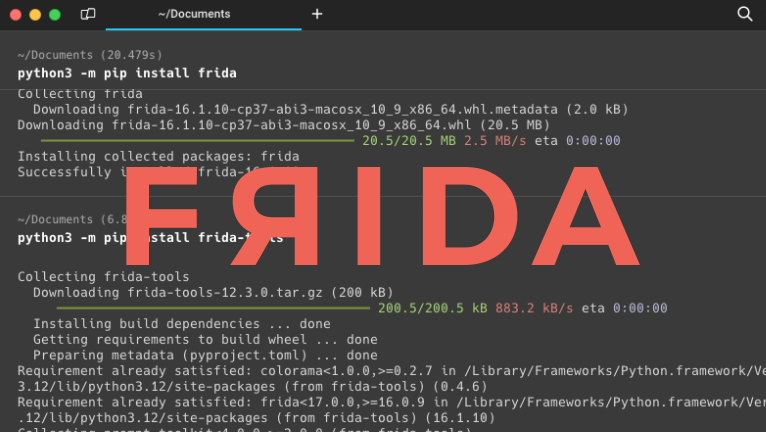
Setting up and configuring Frida for use should be a quick process, typically taking just a few minutes. Installing Frida's CLI tools is uncomplicated, although a few prerequisites must be met on your system before you commence. Ensure that Python (preferably 3.x) is installed. Frida is compatible with operating systems such as Windows, macOS, or GNU/Linux.
pip install frida
pip install frida-toolsHow to inject script with Frida
Injecting a Frida instrumentation script into an iOS device connected via USB can be accomplished with the following command. The -n switch, set as the default option, designates the process name to which the script will attach (the corresponding app must be running before executing this command). Additionally, the -U switch is employed to specify that a USB device is the target, making this option essential for all iOS-related commands.
$ frida -U -n Twitter -l demo1.js