Inject jailbreak tweaks into iOS apps with Azule
Adding features to iOS app is possible through various tools designed to inject jailbreak tweaks into restricted apps. While options like Sideloadly offer a straightforward approach, there are also on-device alternatives such as FlekStore, or Esign enabling users to tweak their apps by injecting tweaks seamlessly. Nevertheless, Azule distinguishes itself with an extensive array of features and configuration options.
What is Azule?
Azule is a tool packed with numerous features tailored to inject jailbreak tweaks into decrypted iOS apps, facilitating the sideloading of packages even on non-jailbroken devices. This versatile application is compatible with macOS, and Linux, and can be directly installed on jailbroken iOS devices, offering users seamless access to enhanced functionalities.
Using Azule is a simple process that involves specifying an IPA file and a tweak, with the tool handling the rest seamlessly. This tweak injection solution supports the importation of custom files and folders, including .deb, .dylib, and .framework files, which are processed and injected into the application. Additionally, other files and folders are copied to the root directory of the app, ensuring a smooth integration of tweaks and customizations.
This CLI tool used to inject iOS jailbreak tweaks into jailed iOS apps can handle importing multiple tweaks at once, works with almost every app-targeted tweak, and supports fetching tweaks through Canister and directly from MobileAPT repos. This means you can download and inject tweaks directly from Havoc or Chariz Repos by providing the tweak bundle ID.
In addition to its primary function of injecting tweaks into iOS apps, Azule provides advanced modifier options. These features include the ability to change an app's version, modify its bundle identifier, adjust its display name, apply fakesigning, eliminate app extensions, remove UISupportedDevices from the app, and even strip away Apple Watch support.
Running Azule directly on your jailbroken device unlocks an additional feature. The ability to fetch and decrypt apps directly from the App Store. This convenient functionality provided by ipatool allows users to fetch and decrypt IPA with specified Apple ID.
Furthermore, this Azule for iOS includes an APT Module with the ability to specify custom repos with packages. Additionally, users can filter out packages originating from Canister and exclude those from APT Sources. They also have the option to bypass the installation of package dependencies. Moreover, the module allows users to tailor repository refreshing settings.
With Azule, users have a comprehensive toolkit for injecting jailbreak tweaks into IPA packages with the option to download the latest substrate and substitute hooking libraries. This CLI tool can be also used to automate the process of creating IPA files with the latest version of tweaks.
How to install Azule
On macOS
Step 1. Clone Azule repository from the official GitHub.
git clone https://github.com/Al4ise/Azule ~/AzuleStep 2. Create a symbolic link to execute the Azule from any location in your terminal.
sudo ln -sf ~/Azule/azule /usr/local/bin/azuleOn Linux
Step 1. Clone Azule repository from the official GitHub.
git clone https://github.com/Al4ise/Azule ~/AzuleStep 2. Create a symbolic link to execute the Azule from any location in your terminal.
sudo ln -sf ~/Azule/azule /usr/local/bin/azuleOn iOS
Step 1. Add the following repositories to your favorite package manager.
https://apt.alfhaily.me/
https://repo.packix.com/
https://level3tjg.me/repo/
https://cydia.akemi.ai/Step 2. Download the latest version of Azule for iOS.
Available Commands
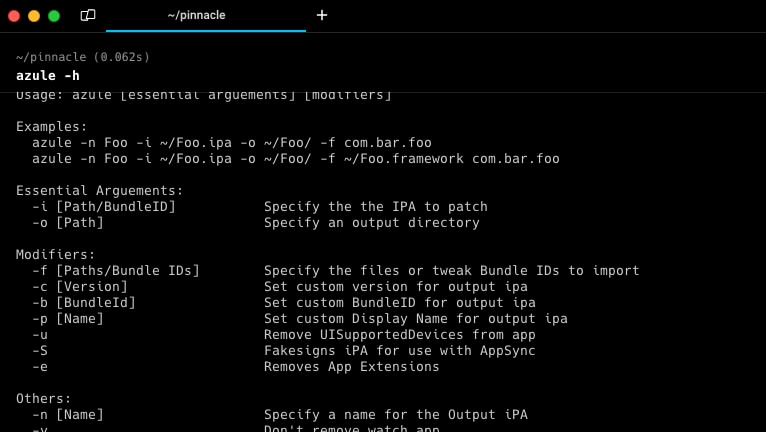
Usage: azule [essential arguements] [modifiers]
Examples:
azule -n Foo -i com.example.foo -x [email protected] password123 -o ~/Foo/ -f com.alaise.example ~/Foo.bundle -a -m
azule -n Foo -i ~/Foo.ipa -o ~/Foo/ -f com.bar.foo
azule -n Foo -i ~/Foo.ipa -o ~/Foo/ -f ~/Foo.framework com.bar.foo
Essential Arguements:
-i [Path/BundleID] Specify the the IPA to patch
-o [Path] Specify an output directory
Modifiers:
-f [Paths/Bundle IDs] Specify the files or tweak Bundle IDs to import
-c [Version] Set custom version for output ipa
-b [BundleId] Set custom BundleID for output ipa
-p [Name] Set custom Display Name for output ipa
-u Remove UISupportedDevices from app
-S Fakesigns iPA for use with AppSync
-e Removes App Extensions
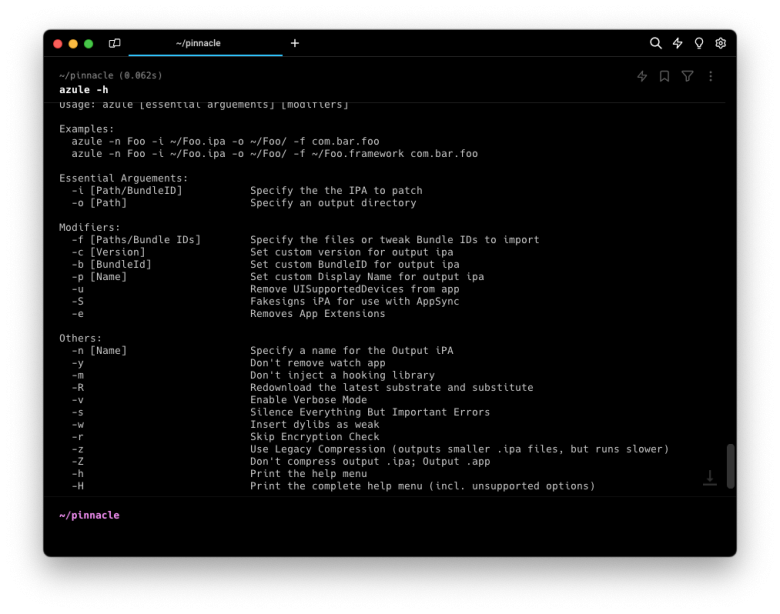
APT Module:
-A [Source URL/Repo List] Specify custom sources to get packages from
-L Ignore packages from Canister
-k Ignore packages from APT Sources
-d Don't install package dependencies
-D Disable refreshing Procursus/Elcubratus repos
Decrypt Module:
-x [Apple ID] [Password] Fetch and decrypt iPA with specified Apple ID
-C [Country Code] Specify country code for ipatool
-g Force Update Apps
-l Don't Update Outdated Apps
Others:
-n [Name] Specify a name for the Output iPA
-y Don't remove watch app
-m Don't inject a hooking library
-R Redownload the latest substrate and substitute
-v Enable Verbose Mode
-s Silence Everything But Important Errors
-w Insert dylibs as weak
-r Skip Encryption Check
-q Ignore errors [Discouraged]
-j Allow for Azule to be ran as root [Discouraged]
-z Use Legacy Compression (outputs smaller .ipa files, but runs slower)
-Z Don't compress output .ipa; Output .app
-h Print the help menu
-H Print the complete help menu (incl. unsupported options)
MacOS/Linux Only:
-U Don't Update Azule on run
-F Forcefully update Azule