How to install Mobile Verification Toolkit (MVT)

Mobile Verification Toolkit (MVT) serves as a valuable tool for streamlining the consensual forensic analysis of iOS devices, enabling the identification of compromise indicators. This innovative toolkit, by the Amnesty International Security Lab, emerged within the framework of the Pegasus Project. Notably, MVT played a pivotal role in uncovering Operation Triangulation and its associated 0-day exploits for iOS.
Key Takeaways
- MVT is the best software to detect if your iPhone was compromised by mercenary spyware like NSO Group Pegasus, Predator Spyware, Operation Triangulation, etc.
- Encrypted backups contain additional records such as Safari history, Safari state, and other pertinent information, enhancing the forensic insights.
Overview
Mobile Verification Toolkit (MVT) is a set of utilities to automate the gathering of forensic traces essential for identifying potential compromises on iOS devices. This toolkit proves invaluable in assessing whether an iPhone has been subject to hacking or unauthorized access. By employing MVT, users can efficiently analyze and ascertain the security status of their iOS devices, ensuring prompt detection and response to any unauthorized activities.
This tool was designed to identify the Pegasus used by governments to take full control over every iOS device without the knowledge of the user by utilizing 0-day and 0-click exploits. MVT facilitates the utilization of public indicators of compromise (IOCs) to conduct scans on mobile devices, identifying potential traces of targeting or infection by recognized spyware campaigns.
This functionality extends to incorporating IOCs published by prominent entities such as Amnesty International and other reputable research groups. Users can leverage Mobile Verification Toolkit (MVT) to enhance their forensic analysis, staying vigilant against known threats and bolstering overall mobile device security.
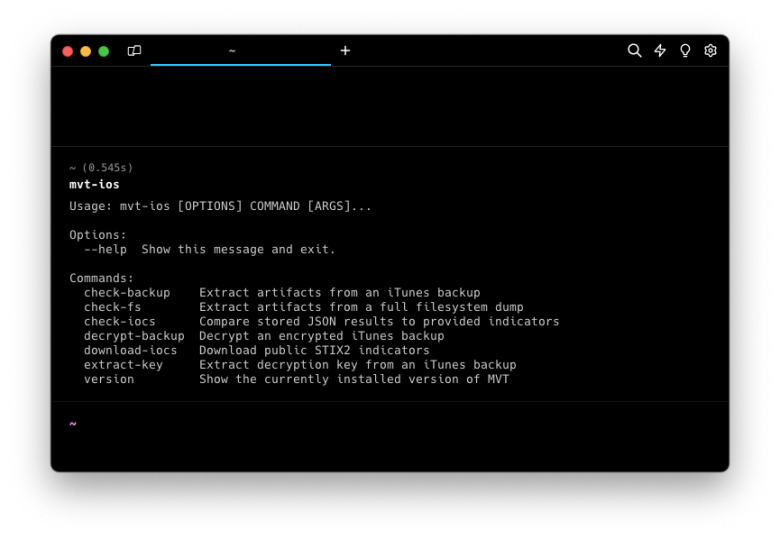
Mobile Verification Toolkit (MVT) exhibits a dynamic range of capabilities that continuously evolve to meet the demands of forensic analysis. These encompass the decryption of encrypted iOS backups, the meticulous processing, and parsing of records sourced from a myriad of iOS system and app databases, logs, and system analytics.
Furthermore, MVT extends its functionality to extract installed applications from Android devices, gather diagnostic information from Android devices through the adb protocol, and compare extracted records against a provided list of malicious indicators in STIX2 format.
What's new
- Convert timezone-aware date-times automatically to UTC.
- Updates SMS module to highlight the new text of Apple notifications.
- Requires the latest cryptography version.
- [auto] Update iOS releases and versions.
- Improvements for SMS module.
- Add uri=True in mvt/ios/modules/base.py.
- Circular reference in SMS module serialization.
- dumpsys_accessibility.py: Spell accessibility correctly.
Additionally, MVT generates JSON logs encompassing extracted records, while also creating separate JSON logs specifically highlighting all detected malicious traces. The toolkit further offers the generation of a unified chronological timeline that encapsulates all extracted records, alongside a dedicated timeline emphasizing the presence of detected malicious traces.
Note: Running MVT on macOS requires Xcode and homebrew to be installed.
MVT supports iTunes backups and system dumps from a jailbroken environment. Most recent version of macOS, these backups are initiated directly from Finder rather than iTunes. Although backups offer only a partial representation of the files stored on the device, they often prove adequate for detecting certain suspicious artifacts.

Notably, encrypted backups, requiring a password for access, contain additional intriguing records that are unavailable in their unencrypted counterparts. These encompass significant data such as Safari history, Safari state, and other pertinent information, enhancing the forensic insights that can be gleaned from the analysis.
MVT enables the extraction of information from the iDevice, providing a comprehensive overview. This includes creating a timeline that meticulously captures every process and app running on the system. Additionally, MVT offers insights into various parameters such as the total number of messages, device identifiers like ID, ECID, GUID, ICCID, MEID, and IMEI, as well as a list of installed apps. Moreover, it sheds light on system components accessed by apps, such as the microphone, offering a thorough analysis of the device's activity and configuration.
Supported Spyware Detection
- NSO Group Pegasus
- Predator Spyware
- RCS Lab Spyware
- Stalkerware
- Surveillance campaign
- Quadream KingSpawn
- Operation Triangulation
- WyrmSpy and DragonEgg
How to install MVT
Mobile Verification Toolkit (MVT) is available for download through PyPI. This streamlined method is equally applicable for Windows, Linux, and macOS users seeking to install the utility. MVT provides two commands mvt-ios and mvt-android for execution from the command line.
brew install python3 libusb sqlite3
pip uninstall urllib3
pip install urllib3
export PATH=$PATH:~/.local/bin
pip3 install mvt
Usage:
mvt-ios decrypt-backup -d $decrypted_backup_directory $backup_directory
mvt-ios check-backup -o $mvt_output_directory $decrypted_backup_directory