How to decrypt iOS backup using pyiosbackup
By default, local iPhone backups are not encrypted, although it's strongly advised to enable encryption for enhanced security. When encryption is enabled, accessing these backups necessitates a password. Utilizing tools such as pyiosbackup, users can conveniently decrypt entire iOS backups or select specific files. This tool is compatible with Linux, macOS, and Windows, offering comprehensive data regarding your iPhone.
Before encrypting an iOS backup, it's necessary to create one. There are several methods to accomplish this task. You can utilize iTunes, and Files, or employ tools such as idevicebackup2 or pymobiledevice3. Those last tools are command-line utilities that can be executed on all major Desktop platforms. pyiosbackup can only decrypt an existing backup.
What is pyiosbackup?
pyiosbackup is a utility created to decrypt iPhone backups. Among the features of pyiosbackup is the ability to decrypt all files within a backup, extract specific files based on their domain and file ID, display statistics regarding a backup, and decrypt all files to a filesystem layout. Utilizing pyiosbackup is a straightforward process, allowing users to easily create their scripts.
Decrypted backups serve various purposes, including recovery and security analytics of installed components, log files, and more. Notably, encrypted backups, with a password, contain additional valuable records unavailable in their unencrypted counterparts.
These encompass crucial data like Safari history, Safari state, and other pertinent information, significantly enhancing the forensic insights gleaned for analysis. Another tool that facilitates the decryption of iOS backups is the Mobile Verification Toolkit (MVT). This command-line utility also provides a feature for decrypting password-protected iOS backups.
How to install pyiosbackup
Although pyiosbackup can be installed directly through the pip package manager for Python packages, it is recommended to install the utility directly from its sources for optimal compatibility. Follow the steps below to install pyiosbackup:
Step 1. Open the terminal app and clone the official GitHub Repository.
git clone https://github.com/matan1008/pyiosbackupStep 2. Execute the command to enter the folder.
cd pyiosbackupStep 3. Use python pip to install pyiosbackup from the sources.
python3 -m pip install --user -U -e .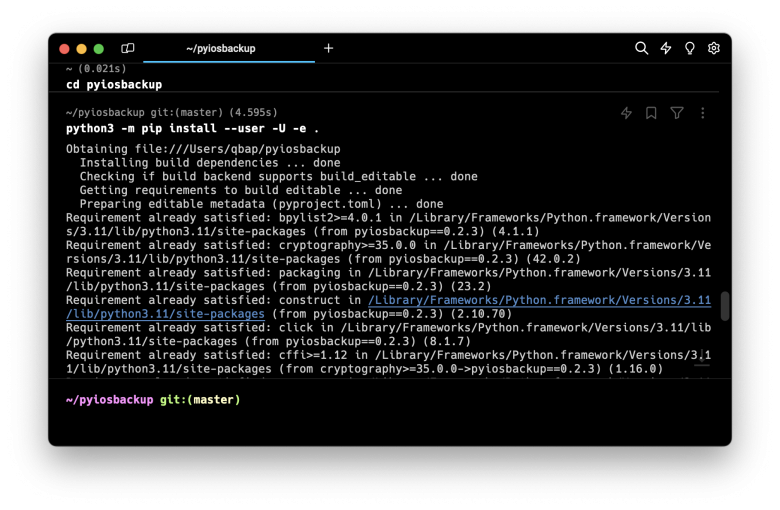
How to decrypt iOS backup using pyiosbackup
Once pyiosbackup is installed on your desktop, you can begin decrypting iOS backups. Several options are available, including full extraction of files, single-file extraction, or extraction by ID. Since pyiosbackup can also be utilized as a library, you can effortlessly create Python scripts to perform various tasks, such as brute-forcing encryption passwords using a dictionary, extracting only specific files for analysis, and more.
After creating the backup, you can decrypt it:
pyiosbackup extract-all $BACKUP_FOLDER -p 1234 --target decryptedYou can also extract single files by their domain and relative path:
pyiosbackup extract-domain-path $BACKUP_FOLDER RootDomain Library/Preferences/com.apple.backupd.plist -p 1234Or by their file ID using the following command with options:
pyiosbackup extract-id $BACKUP_FOLDER a1v323a132dd9caDw4a6d8b44dA7c8049xx1adxf12 -p 1234You can also print some metadata about the backup:
pyiosbackup stats $BACKUP_FOLDER -p 1234Brute force iOS backup password
With a Python script, you can harness pyiosbackup to conduct brute-force attacks on iOS backup passwords. This script can systematically read passwords from the text file, attempting each one until a successful authentication occurs or until the end of the file is reached.
from pyiosbackup import Backup
def test_passwords(backup_path, password_file):
with open(password_file, 'r') as f:
passwords = f.readlines()
for password in passwords:
password = password.strip() # Remove any leading/trailing whitespace or newline characters
print(f"Testing password: {password}")
try:
backup = Backup.from_path(backup_path, password)
for file in backup.iter_files():
print(file.filename)
print(file.last_modified)
print("Password successfully authenticated!")
return # Exit the function if password is correct
except Exception as e:
print(f"Failed to authenticate with password: {password}. Error: {e}")
print("All passwords failed.")
backup_path = 'BACKUP_PATH'
password_file = 'PASSWORD_FILE.txt' # Change this to the path of your password file
test_passwords(backup_path, password_file)Available commands
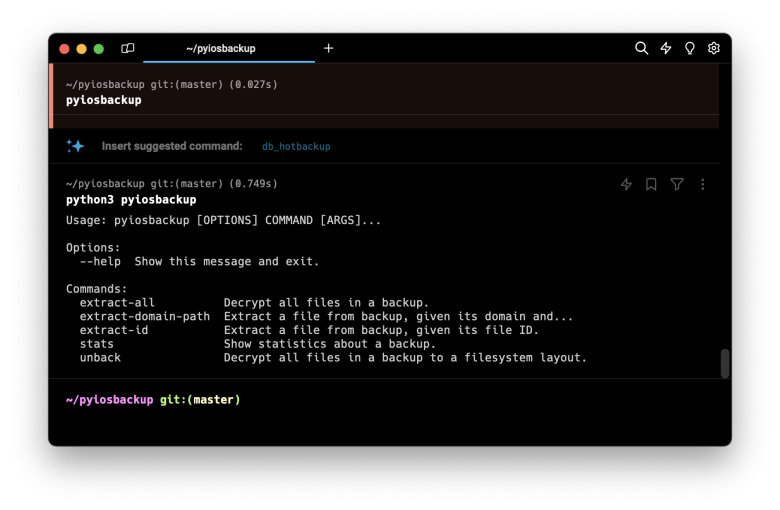
python3 pyiosbackup
Usage: pyiosbackup [OPTIONS] COMMAND [ARGS]...
Options:
--help Show this message and exit.
Commands:
extract-all Decrypt all files in a backup.
extract-domain-path Extract a file from backup, given its domain and...
extract-id Extract a file from backup, given its file ID.
stats Show statistics about a backup.
unback Decrypt all files in a backup to a filesystem layout.
p Password for decryption (-p 1234)



