Detect Pegasus spyware on iPhone

Pegasus, by NSO Group, stands as a potent example of covert surveillance technology. Engineered to discreetly infiltrate iOS and Android mobile devices, it epitomizes the intersection of innovation and intrusion. Although initially heralded as a tool to combat crime and terrorism, Pegasus has found nefarious applications in the hands of numerous governments worldwide. Under the guise of national security, it has been systematically employed to spy on journalists, legal practitioners, and political dissidents.
NSO Group's Pegasus demonstrated the capability to seize control of targeted devices, requiring no action on the part of the users. Leveraging both zero-day vulnerabilities and zero-click exploits, it injected malware into victims' devices, thereby enabling full surveillance. This included unauthorized access to and retrieval of sensitive data such as photos, GPS coordinates, text messages, emails, and more, further underscoring the extent of its invasive capabilities. Pegasus became famous because it was used against civilians worldwide.
Pegasus was accessed by government clients for money and was designed to "gather data from the mobile devices of specific individuals suspected to be involved in serious criminal activities and terrorism." Pegasus boasts a range of sophisticated capabilities, enabling remote installation on smartphones without any action required from the device owner.
Once deployed, it grants clients full control over the targeted device, facilitating access to messages from encrypted platforms like WhatsApp and Signal, Photos, call history, Contacts, and location, as well as enabling the activation of the microphone and camera.
NSO Group's Pegasus was meticulously engineered to evade detection by both users and researchers. However, despite its stealthy design, the software leaves behind subtle traces that can be indicative of its installation on the device. Amnesty International Security Lab released MVT allowing users to detect if Pegasus spyware was installed on iPhone or Android.
How to detect Pegasus spyware on iOS
To ascertain whether the Pegasus spyware has been installed on your iPhone, it is necessary to first create a backup of your device. Subsequently, employing a tool like the MVT becomes imperative in determining the presence of NSO Group's spyware on your iDevice.
MVT utilizes various indicators such as malware, relationships, bundled files, domain names, and Apple IDs associated with compromising your device, as well as monitoring running processes to effectively detect the installation of Pegasus. MVT uses pegasus.stix2 indicator to identify and detect Pegasus spyware from your iPhone backup file.
Note: Encrypted iOS backups contain additional intriguing records that are unavailable in their unencrypted counterparts. These encompass significant data such as Safari history, Safari state, and other pertinent information, enhancing the forensic analysis.
Follow those steps to detect Pegasus spyware on iOS:
Step 1. Install Mobile Verification Toolkit on Desktop.
Step 2. Connect your iPhone to your computer through a USB cable.
Step 3. Create an iPhone Backup (encrypted) using iTunes or command line tools.
Step 4. Open your preferred terminal application.
Step 5. Excetut the following command to decrypt the iOS backup.
mvt-ios decrypt-backup -d $decrypted_backup_directory $backup_directoryStep 6. Enter the password for encryption of the iOS backup file.
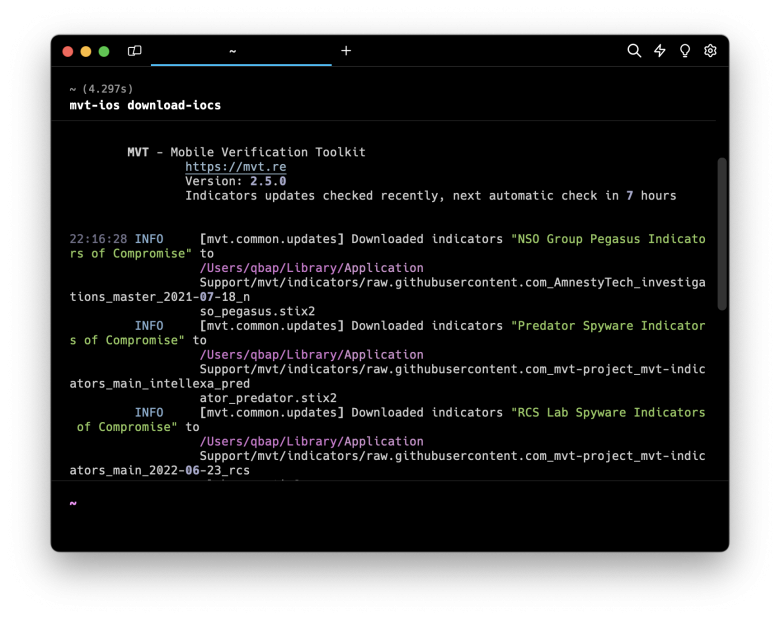
Step 7. Update MVT indicators to the latest version.
mvt-ios download-iocsStep 8. Scan iOS backup with MVT to determine if Pegasus spyware was installed.
mvt-ios check-backup -o $mvt_output_directory $decrypted_backup_directoryStep 9. View the command line prompt for Pegasus spyware detection status.
Step 10. For further analysis, you can navigate through $mvt_output_directory files.