Checkm8 exploit for A5–A11 Apple devices on iOS 12 – iOS 16
On Sep 27, 2019 axi0mX released checkm8 (read “checkmate”), a permanent unpatchable bootrom exploit for hundreds of millions of iOS devices. In 2022 the exploit is still running on modern iOS 15 and iOS 16 jailbreaks for A9 – A11 SoC Apple devices.
What is Checkm8?
Checkm8 is a bootrom exploit with a CVE ID of CVE-2019-8900 used to run unsigned code on iOS, iPadOS, tvOS, and watchOS, with processors between an A5 and an A11. It is used mostly to jailbreak Apple devices, and the exploit is the heart of the popular checkra1n jailbreak.
Jailbreaks based on checkm8 are semi-tethered jailbreaks, as the exploit works by taking advantage of a use-after-free in the USB DFU stack. It is used by ipwndfu, Fugu14, checkra1n, Palera1n, Blizzard Jailbreak, ayakurume, and a couple of other tools to exploit iOS 12 – iOS 17.
Using checkm8 exploit, it is possible to execute the code only when connecting your iPhone or iPad in DFU mode to the computer via a USB cable. checkra1n allows you to jailbreak iOS 12 up to iOS 14 with support for tweaks and was never updated to add support for iOS 15.
Checkm8 bootrom exploit is also able to execute code iOS 15. Nebula, the developer behind Palera1n Jailbreak released the first iOS 15 jailbreak based on checkm8 with tweak injection support on iOS 15.0 – 15.3.1. It also works up to iOS 15.7 on A9-A11 devices without tweaks.
How it works? In C programming language, the function malloc should return NULL if it is unable to allocate memory of the requested size. Caller should check if the returned pointer is NULL and handle the error. In S5L8920 bootrom this function is not implemented correctly. When it is unable to allocate memory, instead of NULL it returns a pointer to memory address 0x8.
Checkm8 takes advantage of this vulnerability, making it possible to execute code on iOS, iPadOS, tvOS, and watchOS. This bug is on all Apple A5 – A11 devices and can't be fixed. Therefore, iOS 16 is vulnerable and can be jailbroken on supported devices.
Note: Most generations of iPhones and iPads are vulnerable and be can exploited using checkm8: from iPhone 4S (A5 chip) to iPhone 8 and iPhone X (A11 chip).
New devices such as iPhone 14, iPhone 14 Pro, iPhone 13 Mini, iPhone 13, iPhone 13 Pro, iPhone 13 Pro Max, iPhone 12, iPhone 12 Pro, iPhone 12 Mini, iPhone 12 Pro Max iPhone 11 Pro, iPhone 11, iPhone 11 Pro Max, iPhone XR, iPhone XS Max, and iPhone XS are checkm8 proof.
axi0mX, the developer behind checkm8 exploit, released the source code under GPL-3.0 license, making it possible to implement for third-party tools. What's more, checkm8 exploit is a part of his ipwndfu open-source jailbreak tool for iOS devices, written in Python and Assembly.
On top of that, checkm8 exploit for A5–A11 is also implemented by the SSH Ramdisk Script to create and boot an SSH ramdisk on checkm8 devices. This tool can be used to install permanently IPA files on stock iOS. TrollStore IPA Installer was sideloaded this way.
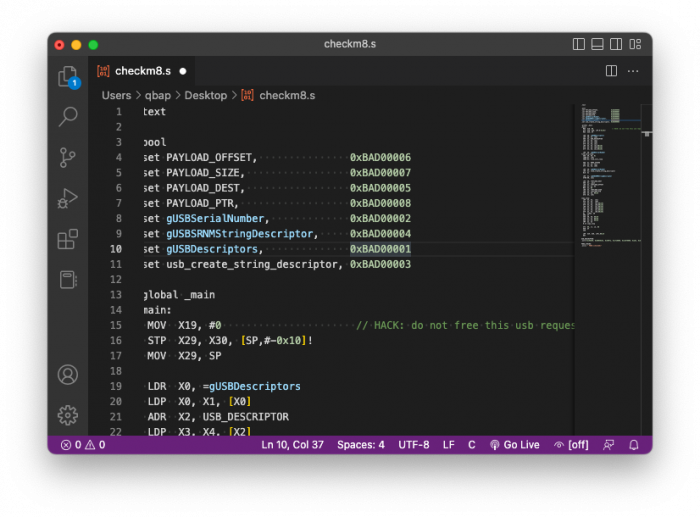
checkm8 Source Code
checkm8 exploit was written in Assembly. Below, you can view the checkm8 exploit source code for all arm64 devices that include all variations of iPhone 5S, iPhone 5S, iPhone SE, iPhone 7, iPhone 8, and iPhone X. checkm8 source code was published through ipwndfu jailbreak.
.text
.pool
.set PAYLOAD_OFFSET, 0xBAD00006
.set PAYLOAD_SIZE, 0xBAD00007
.set PAYLOAD_DEST, 0xBAD00005
.set PAYLOAD_PTR, 0xBAD00008
.set gUSBSerialNumber, 0xBAD00002
.set gUSBSRNMStringDescriptor, 0xBAD00004
.set gUSBDescriptors, 0xBAD00001
.set usb_create_string_descriptor, 0xBAD00003
.global _main
_main:
MOV X19, #0 // HACK: do not free this usb request
STP X29, X30, [SP,#-0x10]!
MOV X29, SP
LDR X0, =gUSBDescriptors
LDP X0, X1, [X0]
ADR X2, USB_DESCRIPTOR
LDP X3, X4, [X2]
STP X3, X4, [X0]
STP X3, X4, [X1]
LDP X3, X4, [X2,#0x10]
STP X3, X4, [X0,#0x10]
STP X3, X4, [X1,#0x10]
LDR X0, =gUSBSerialNumber
find_zero_loop:
ADD X0, X0, #1
LDRB W1, [X0]
CBNZ W1, find_zero_loop
ADR X1, PWND_STRING
LDP X2, X3, [X1]
STP X2, X3, [X0]
LDR X0, =gUSBSerialNumber
LDR X1, =usb_create_string_descriptor
BLR X1
LDR X1, =gUSBSRNMStringDescriptor
STRB W0, [X1]
LDR X0, =PAYLOAD_DEST
ADR X1, _main
LDR X2, =PAYLOAD_OFFSET
ADD X1, X1, X2
MOV X2, #0
LDR X3, =PAYLOAD_SIZE
LDR X4, =PAYLOAD_PTR
ADD X5, X0, #0x18
STR X5, [X4]
copy_loop:
LDP X3, X4, [X1]
STP X3, X4, [X0]
LDP X3, X4, [X1,#0x10]
STP X3, X4, [X0,#0x10]
LDP X3, X4, [X1,#0x20]
STP X3, X4, [X0,#0x20]
LDP X3, X4, [X1,#0x30]
STP X3, X4, [X0,#0x30]
DC CIVAC, X0
DMB SY
ADD X0, X0, #0x40
ADD X1, X1, #0x40
ADD X2, X2, #0x40
CMP X2, X3
B.CC copy_loop
SYS #0, c7, c5, #0
DSB SY
ISB
LDP X29, X30, [SP],#0x10
RET
USB_DESCRIPTOR:
.word 0x190209, 0x80050101, 0x409fa, 0x1fe0000, 0x21070000, 0xa01, 0x8, 0x0
PWND_STRING:
.asciz " PWND:[checkm8]"Checkm8 Jailbreaks
Since the release day, checkm8 exploit has been used by many tools to jailbreak iOS. Some of them are published and ready to use, others are just in development. Only Palera1n for iOS 15 allows you to install tweaks, other tools are not released yet or are useful for developers only.
- palera1n for iOS 15.0 – iOS 17.
- Palera1n Windows for iOS 15.0 – iOS 17.
- WinRa1n for iOS 12 – iOS 17.
- checkra1n for iOS 12 – iOS 14.8.1.
- iRa1n for iOS 12 – iOS 14.8.1.
- Fugu14 for iOS 14 – iOS 14.8.1.
- ipwndfu for iPhone 3GS.
- kok3shi15 for iOS 15.
- kok3shi16 for iOS 16 – iOS 16.2.
- Blizzard Jailbreak for iOS 15 and iOS 16.
- ayakurume for iOS 16.
- checkn1x for iOS 12 – iOS 14.8.1.
- Odysseyn1x for iOS 12 – iOS 14.8.1.
- Project36 for iOS 15.
- checkra1n for Windows – iOS 12 up iOS 14
checkm8 iCloud Bypass tools
checkm8 exploit is also a big part in the development of all iCloud Bypass tools allowing users to remove the Activation Hello Screen and access the device's Home Screen on iOS 12 – iOS 16. Most of the tools require a jailbreak with palera1n or checkra1n and don't work with a SIM card, however, Wi-Fi is working allowing you to sideload apps, and access the App Store.
- FrostByte for iOS 15 – iOS 16.5.
- iSkip for iOS 15 – iOS 16.
- Blackw0rm for iOS 12 – iOS 14.
- GodsHand for iOS 13 – iOS 16.
- Euphoria Activator12 for iOS 12 – iOS 14.
- Goldra1n for iOS 15 – iOS 16.
- GreenSn0w for iOS 12 – iOS 12.5.6.
- BlackRa1n for iOS 15.
- DarkRa1n for iOS 15 – iOS 16.
- iPass for iOS 15 – iOS 16.
Comments
J 2 months ago
Hi Kuba,
My device is passcode locked (my girlfriend forgot the code). I need to reset it and I have limited internet data. I downloaded a beta IPSW but idevicerestore can only use it if I have your bootrom exploit in place. I am on Linux. Is it possible to bootrom exploit the locked phone? It's iPhone 13.Thank you!
qbap 2 months ago
You can't. There is no working solution for the iPhone 13. Apple patched all exploits.